SSO LDAP setup for Filestash
This document provides a detailed guide on how to set up the LDAP connector in Filestash. It is divided into 3 main sections:
- Technical Requirements: the prerequisites to follow this guide
- Basic Setup: step by step instructions for the most basic LDAP integration
- Advanced Setup: describes how to use LDAP attributes to generate dynamic storage connections
Requirements
Filestash integrates with all LDAP compliant IDPs (including Active Directory, Entra ID, openLDAP, ..etc.) To test this integration, you will need the details of your LDAP server. For the purposes of this documentation, we will create a dummy test instance running locally with the following configuration:
- hostname: localhost
- port: 3890
- bind DN: cn=admin,ou=people,dc=example,dc=com
- bind DN Password: password
- base DN: ou=people,dc=example,dc=com
This local test LDAP server was created via docker using this command:
[entrypoint] Copying the default config to /data/lldap_config.toml
[entrypoint] Edit this file to configure LLDAP.
> Setup permissions..
> Starting lldap..
...
Tip: this server has a web UI for user management available by visiting http://localhost:17170.
Basic Setup
A basic setup involves 2 steps:
STEP 1: Configure the IDP settings. Here’s an example configuration:
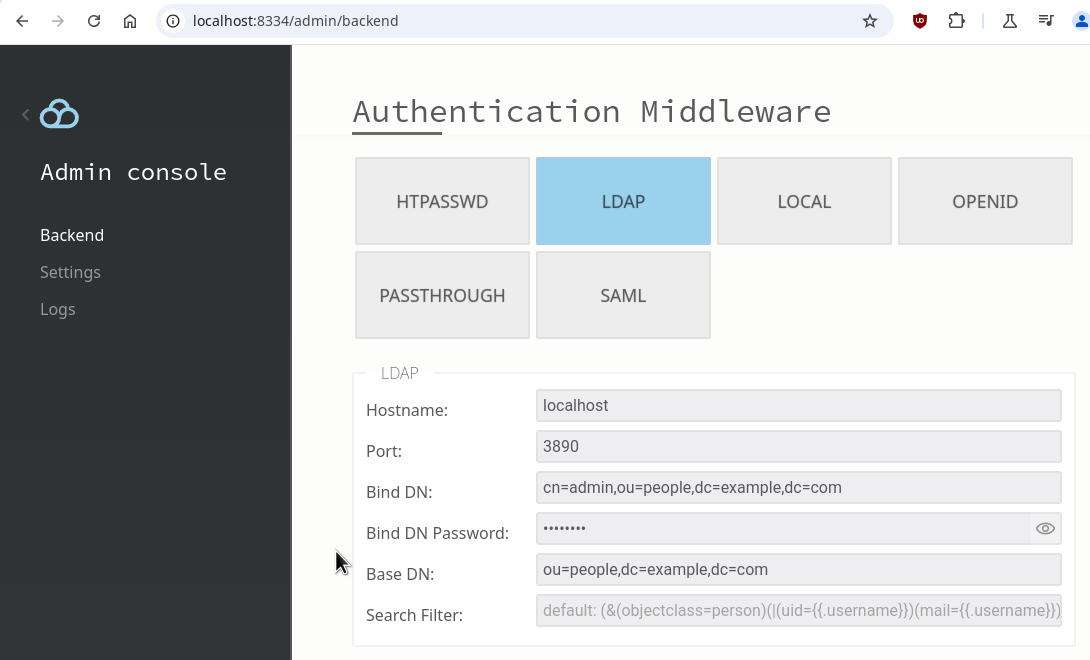
STEP 2: Link your IDP to the chosen storage:
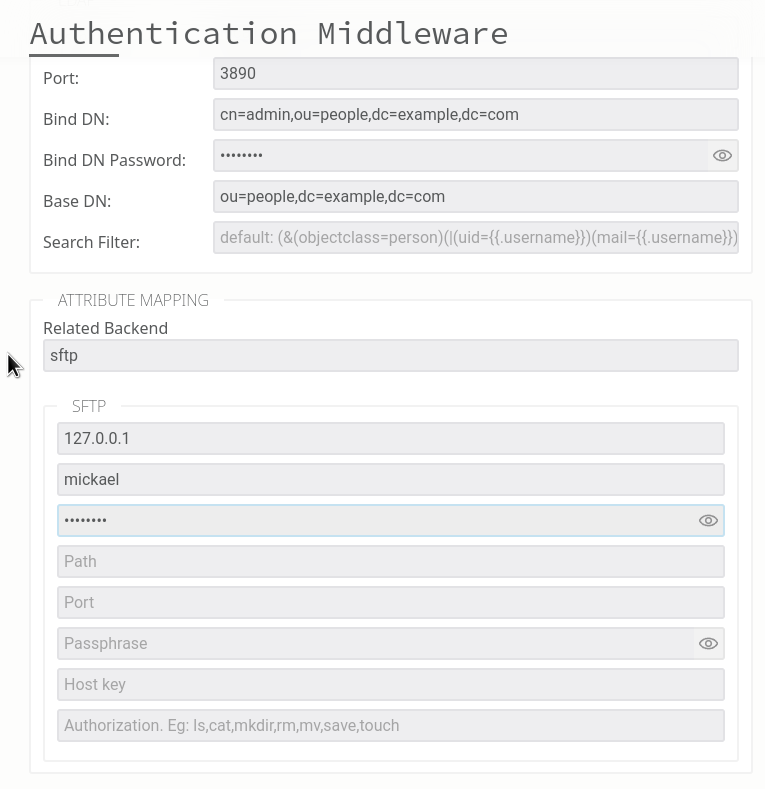
Once configured, users logging in via SFTP will be greeted with this login page:
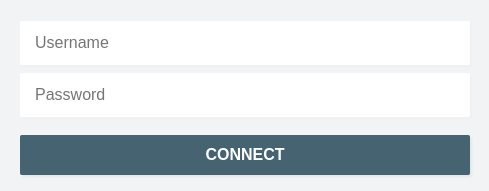
Advanced Setup
Now that we’ve covered the basics, let’s dive into the cool stuff: using LDAP attributes to create dynamic connection rules. The first step is understanding the attributes your LDAP server provides. These attributes will be visible in the logs if you set the logging level to DEBUG within /admin/logs:
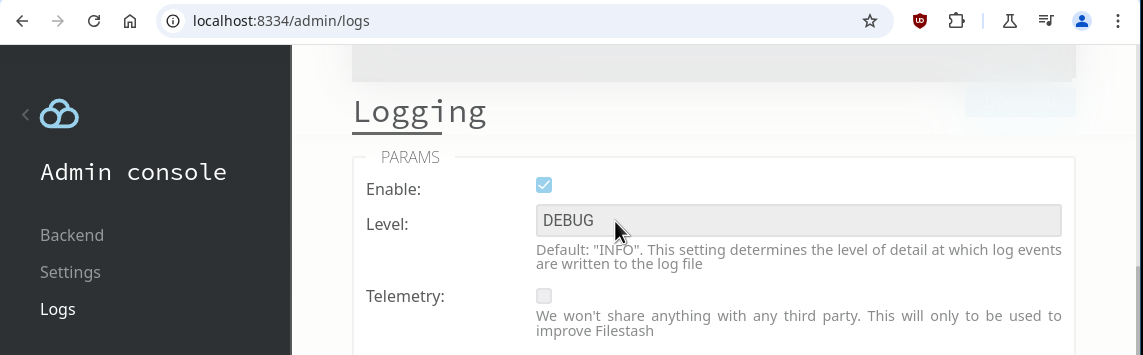
In my case, the log looked like this:
...
2024/12/09 15:25:26 SYST DEBUG LDAP Attributes => createtimestamp[2024-12-09T03:21:29.702435383+00:00] entryuuid[c503698e-f069-3d32-9f94-ecbdf1919d80] objectclass[inetOrgPerson,posixAccount,mailAccount,person] uid[admin] password[*****] cn[Administrator]
...
All these attributes (eg: createtimestamp, entryuuid, objectclass, uid, password, cn) can be utilised to configure the connection to your storage. For this example, let’s setup rules where Administrators have full access to the entire filesystem, while regular users are restricted to read only their own folder:
- path: {{ if .sub | contains "admin" }}/{{ else }}/home/{{ .sub }}/{{ end }}
- authorization: ls,cat{{ if .sub | contains "admin" }},touch,mkdir,mv,rm{{ end }}

The possibilities are endless. Behind the scenes, you can leverage the entire Go templates ecosystem, enhanced with custom functions to support a wide range of use cases.
If you encounter any issues, feel free to reach out to support, and we’ll help resolve them.
